02-Endpoint-Threat-Detection: 02-BlueTeam-Report
- TrilloSec

- Feb 23
- 18 min read
Updated: Feb 24

Blue Team Report: Endpoint Detection & Response (FIN7)
Project: 02-Endpoint-Threat-Detection
Author: TrilloSec
Date: 2025-02-23
1. Executive Summary
1.1 Purpose
The purpose of this Blue Team report is to assess, detect, and respond to the emulated FIN7 threat scenario targeting endpoint systems. This simulation aimed to test the organization’s detection capabilities, response procedures, and overall security posture against advanced persistent threats (APTs). By simulating realistic attack techniques—such as phishing-based initial access, LOLBins abuse, AMSI bypasses, and persistence mechanisms—the report highlights areas of improvement within the Security Operations Center (SOC). Findings and recommendations are provided to enhance detection capabilities, streamline response workflows, and improve the SOC’s readiness against similar future threats.
1.2 Security Effectiveness Metrics (Pre-Test vs. Post-Test)
# | Metric | Pre-Test | Post-Test | Key Takeaway |
1 | Payload Execution Success | 100% | 100% | Payload executed successfully before detection measures activated. |
2 | Privilege Escalation Success | 100% | 0% | Detection prevented privilege escalation attempts. |
3 | Persistence Success | 100% | 0% | Persistence mechanisms were blocked and did not succeed. |
4 | Threat Containment Rate | No Containment | 100% | SOC successfully contained the threat after detection. |
5 | Detection Time (Time-to-Detect - TTD) | Not Detected | < 1 minute | Suspicious activity was detected within one minute. |
6 | Containment Time (Time-to-Containment - TTC) | No Containment | 5 minutes | Threat was isolated five minutes after initial detection. |
2. Detection & Analysis
This section details how the attack was initially detected, key indicators of compromise, and the improvements made to enhance threat detection.
2.1 Pre-Test Analysis
Before implementing new detection rules, an initial assessment was conducted to evaluate the effectiveness of the existing security controls and logging configurations. The evaluation revealed that while Sysmon was enabled on endpoints, coverage for key events—such as registry modifications, scheduled task creations, and certain LOLBins executions—was either limited or absent. AMSI logging was inconsistently applied, reducing visibility into PowerShell-based attacks and in-memory executions. Additionally, although basic Splunk queries were in place, there were no targeted detection rules for persistence mechanisms or advanced C2 channels. This pre-test analysis provided a baseline for identifying detection gaps and guided the development of enhanced monitoring strategies deployed during this simulation.
Delivery - Pretest

Exploitation - Pretest

Installation - Pretest

Command and Control (C2) - Pretest
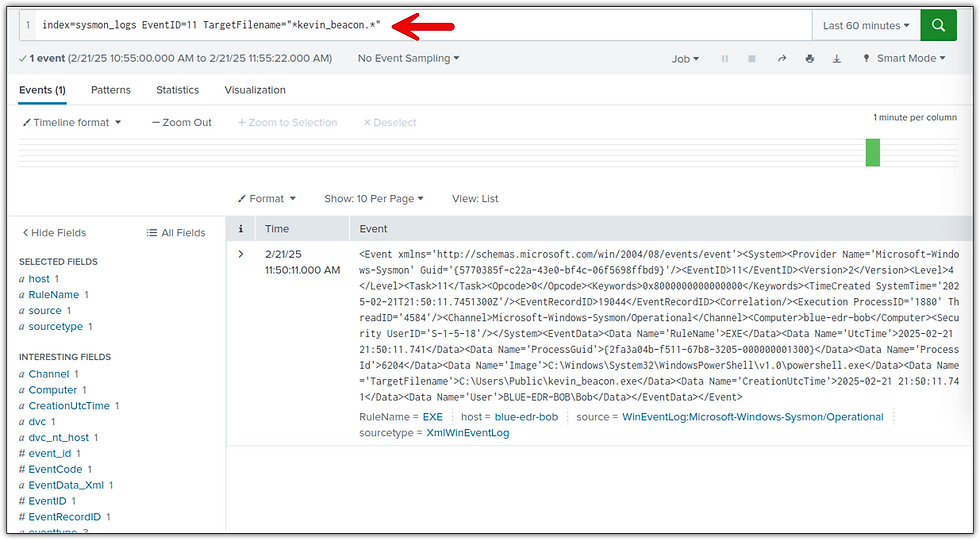
Actions on Objectives (Impact) - Pretest

2.2 Indicators Of Compromise (IOCs)
A list of key artifacts and behaviors observed during the phishing attack, including filenames, processes, network connections, and command-line executions.
Type | Indicator | Description |
Filename | Fake_Invoice_2024.pdf.lnk | Malicious LNK file disguised as an invoice. |
Filename | payload.ps1 | First-stage PowerShell script downloaded by LNK execution. |
Filename | stage2exe.ps1 | Second-stage PowerShell script that downloads and executes the .EXE C2 payload. |
Filename | stage2dll.ps1 | Second-stage PowerShell script that downloads and executes the .DLL C2 payload. |
Filename | kevin_beacon.exe | C2 payload executed on the victim machine. |
Filename | kevin_beacon.dll | C2 payload executed on the victim machine. |
URL | URL hosting the first-stage PowerShell payload. | |
URL | URL hosting the second-stage PowerShell with primary .EXE payload. | |
URL | URL hosting the final C2 beacon executable. | |
URL | URL hosting the obfuscated execution flow to second-stage PowerShell with alternate .DLL payload. | |
URL | URL hosting the second-stage PowerShell with alternate .DLL payload. | |
URL | URL hosting the final C2 beacon DLL. | |
C2 Address | 10.26.0.9:443 | C2 server IP used for Meterpreter callback. |
C2 Traffic | HTTPS (T1071.001) | C2 communication over encrypted web traffic. |
C2 Traffic | TCP (T1071.004) | C2 communication over unencrypted TCP traffic to a port over 1024. |
Impact | URL forced open on the victim’s browser (RickRoll). |
2.3 Optimized Detection Rules
This section presents the updated Sysmon configurations and Splunk queries that were implemented to detect malicious activity more effectively.
Sysmon Configuration
Delivery: Detect Malicious Email Attachments and File Drops
<!-- Detect Suspicious PowerShell Commands -->
<ProcessCreate onmatch="include">
<CommandLine condition="contains">IEX</CommandLine>
<CommandLine condition="contains">DownloadString</CommandLine>
<CommandLine condition="contains">DownloadFile</CommandLine>
<CommandLine condition="contains">Invoke-WebRequest</CommandLine>
<CommandLine condition="contains">Invoke-Expression</CommandLine>
<CommandLine condition="contains">curl</CommandLine>
<CommandLine condition="contains">wget</CommandLine>
</ProcessCreate>
<!-- Detect Dropped Executables or DLLs in Public/Temp Folders -->
<FileCreate onmatch="include">
<TargetFilename condition="contains">\\Users\\Public\\</TargetFilename>
<TargetFilename condition="end with">.exe</TargetFilename>
<TargetFilename condition="end with">.dll</TargetFilename>
</FileCreate>Exploitation: Detect AMSI Bypass Attempts
<!-- Event ID 1: Process Creation -->
<ProcessCreate onmatch="include">
<Image condition="end with">powershell.exe</Image>
<CommandLine condition="contains">amsi</CommandLine>
</ProcessCreate>
<ProcessCreate onmatch="include">
<Image condition="end with">powershell.exe</Image>
<CommandLine condition="contains">bypass</CommandLine>
</ProcessCreate>
<ProcessCreate onmatch="include">
<Image condition="end with">powershell.exe</Image>
<CommandLine condition="contains">Reflection.Assembly</CommandLine>
</ProcessCreate>
<ProcessCreate onmatch="include">
<Image condition="end with">powershell.exe</Image>
<CommandLine condition="contains">Add-Type</CommandLine>
</ProcessCreate>
<ProcessCreate onmatch="include">
<Image condition="end with">powershell.exe</Image>
<CommandLine condition="regex">.*(New-Object\s+System\.Net\.WebClient|IEX|DownloadString).*</CommandLine>
</ProcessCreate>
<!-- Event ID 10: Process Access (Catches memory manipulation attempts like WriteProcessMemory) -->
<ProcessAccess onmatch="include">
<SourceImage condition="end with">powershell.exe</SourceImage>
<TargetImage condition="contains">amsi.dll</TargetImage>
<GrantedAccess condition="contains">0x1F0FFF</GrantedAccess> <!-- Full access permission often used in process injection -->
</ProcessAccess>
<!-- Event ID 8: CreateRemoteThread (Common in memory-based AMSI bypass techniques) -->
<CreateRemoteThread onmatch="include">
<SourceImage condition="end with">powershell.exe</SourceImage>
<TargetImage condition="contains">amsi.dll</TargetImage>
</CreateRemoteThread>Installation: Detect Persistence via Registry and Scheduled Tasks
<!-- Detect Registry Key Modifications (Run & RunOnce Keys) -->
<RegistryEvent onmatch="include">
<TargetObject condition="contains">\\Software\\Microsoft\\Windows\\CurrentVersion\\Run</TargetObject>
</RegistryEvent>
<RegistryEvent onmatch="include">
<TargetObject condition="contains">\\Software\\Microsoft\\Windows\\CurrentVersion\\RunOnce</TargetObject>
</RegistryEvent>
<!-- Detect Scheduled Task Creation -->
<ProcessCreate onmatch="include">
<CommandLine condition="contains">schtasks</CommandLine>
</ProcessCreate>C2: Detect Suspicious Network-Based C2 Activity
<!-- Detect Connections to Known C2 Ports -->
<NetworkConnect onmatch="include">
<DestinationPort condition="is">4444</DestinationPort>
<DestinationPort condition="is">1337</DestinationPort>
<DestinationPort condition="is">8080</DestinationPort>
<DestinationPort condition="is">9001</DestinationPort>
</NetworkConnect>
<!-- Detect Connections to High Ports Above 1024 (Excluding 80, 443, 8443) -->
<NetworkConnect onmatch="include">
<DestinationPort condition="greater_than">1024</DestinationPort>
<DestinationPort condition="is not">80</DestinationPort>
<DestinationPort condition="is not">443</DestinationPort>
<DestinationPort condition="is not">8443</DestinationPort>
</NetworkConnect>Actions on Objectives: Detect Forced System Impact Demonstration
<!-- Detect Forced Execution of Microsoft Edge (msedge.exe) -->
<ProcessCreate onmatch="include">
<Image condition="end with">msedge.exe</Image>
</ProcessCreate>Splunk Queries
Delivery: Detect Malicious Email Attachments and File Drops
(
index=sysmon_logs EventID=1
(CommandLine="*IEX*" AND (CommandLine="*DownloadString*" OR CommandLine="*DownloadFile*" OR CommandLine="*Invoke-WebRequest*" OR CommandLine="*Invoke-Expression*" OR CommandLine="*curl*" OR CommandLine="*wget*"))
)
OR
(
index=sysmon_logs EventID=11
(TargetFilename="*\\Users\\Public\\*.exe" OR TargetFilename="*\\Users\\Public\\*.dll")
)Exploitation: Detect AMSI Bypass Attempts
index=sysmon_logs EventID=1 Image="*\\powershell.exe" (
CommandLine="*amsi*"
OR CommandLine="*bypass*"
OR CommandLine="*Reflection.Assembly*"
OR CommandLine="*Add-Type*"
OR CommandLine="*DownloadString*"
OR CommandLine="*IEX*"
)Installation: Detect Persistence via Registry and Scheduled Tasks
(
index=sysmon_logs EventID=13
(TargetObject="*\\Software\\Microsoft\\Windows\\CurrentVersion\\Run*" OR TargetObject="*\\Software\\Microsoft\\Windows\\CurrentVersion\\RunOnce*")
)
OR
(
index=sysmon_logs EventID=1
CommandLine="*schtasks*"
)C2: Detect Suspicious Network-Based C2 Activity
index=sysmon_logs EventID=3
(
(DestinationPort IN (4444, 1337, 8080, 9001))
OR
(
DestinationPort > 1024
AND NOT (DestinationPort IN (80, 443, 8443))
)
)Actions on Objectives: Detect Forced System Impact Demonstration
index=sysmon_logs EventID=1
Image="*\\msedge.exe"2.4 Response Workflow (NIST Framework)
An overview of the incident response process, structured according to the NIST Cybersecurity Framework (CSF), covering detection, analysis, containment, eradication, and recovery.
Phase | Actions Taken |
Detection | Leveraged Sysmon logs, Splunk SIEM queries, and YARA scans to detect suspicious activities such as LOLBins execution, file drops, and AMSI bypass attempts. |
Analysis | Investigated detected events by correlating process creation, file modification, and network connection logs. Verified persistence mechanisms through registry key analysis and scheduled task enumeration. |
Containment | Isolated the affected host using LimaCharlie and blocked execution of LOLBins (mshta.exe, rundll32.exe) through Group Policy to prevent further payload execution. |
Eradication | Removed malicious files (kevin_beacon.dll), and cleaned registry keys used for persistence. Verified removal using PowerShell commands and Splunk queries. |
Recovery | Restored system configurations to default settings, re-enabled AMSI protections, and ensured proper logging was active to monitor for potential reinfection attempts. Validated recovery by rerunning detection queries. |
Note: Windows Defender was temporarily disabled on the victim VM only to allow execution of the simulated payload. This was done solely within the controlled home lab environment for testing purposes and does not reflect enterprise security configurations.
2.5 MITRE ATT&CK Mapping
A mapping of the observed attack techniques to the MITRE ATT&CK framework, demonstrating how each tactic was detected and highlighting areas for improvement.
Tactic | Technique | MITRE ID | Detection Method | Detection Gap & Fix |
Initial Access | Spear Phishing Attachment (LNK in ZIP) | T1566.001 | Detected via email gateway logs and Splunk queries for ZIP attachments with embedded LNK files. | Initial detection missed ZIP-embedded LNKs; adjusted email gateway rules and attachment scanning. |
Resource Development | Malicious Payload Creation | T1583.001 | Detected via YARA rules scanning build environments for known payload creation patterns. | No detection initially; added YARA-based scans for weaponized LNK and PowerShell payload creation. |
Execution | User Execution (Malicious Shortcut File) | T1204.002 | Monitored with Sysmon Event ID 1 and Splunk queries detecting explorer.exe spawning .lnk files and PowerShell. | Logging was insufficient; enabled parent-child process tracking in Sysmon for LNK executions. |
Execution | Command and Scripting Interpreter: PowerShell | T1059.001 | Detected with Sysmon Event ID 1, Event ID 4104 (script block logging), and Splunk queries monitoring IEX usage. | Enabled PowerShell script block logging; improved Splunk detections for IEX and remote payload fetches. |
Defense Evasion | System Binary Proxy Execution: MSHTA | T1218.005 | Identified via Sysmon logs and Splunk queries monitoring mshta.exe with remote URLs or abnormal parent processes. | Detection only covered direct mshta.exe calls; expanded rules to detect PowerShell→MSHTA pivoting. |
Defense Evasion | AMSI Bypass | T1562.001 | Detected with Splunk queries searching for commands referencing amsi.dll, Reflection.Assembly, or VirtualProtect. | AMSI bypass initially undetected; added process memory monitoring and enhanced PowerShell logging. |
Persistence | Registry Run Keys/Startup Folder | T1547.001 | Detected with Sysmon Event ID 13 and Splunk queries for modifications to HKCU:\Software\Microsoft\Windows\CurrentVersion\Run. | Added targeted alerts for registry key modifications referencing LOLBins (rundll32.exe, mshta.exe). |
Command and Control | Ingress Tool Transfer | T1105 | Detected via Sysmon Event ID 11 (file creation logs) and Splunk network traffic analysis of suspicious downloads. | No initial download detection; implemented rules for file writes to public and temp directories. |
Command and Control | Application Layer Protocol: HTTPS | T1071.001 | Monitored using Sysmon Event ID 3 and Splunk queries targeting abnormal HTTPS connections from LOLBins. | Gaps in outbound HTTPS detection resolved by adding destination IP filtering and process correlation. |
Impact | Defacement: Internal Defacement (GUI Manipulation) | T1491.001 | Detected via Sysmon Event ID 10 for process access and Splunk queries for unauthorized browser executions. | Expanded detection for forced browser launches with suspicious command lines (e.g., msedge.exe with unusual arguments). |
3. Mitigation & Response
This section outlines the response actions taken after detecting the phishing attack, including containment, eradication, and recommendations for strengthening defenses.
3.1 Post-Test Analysis
Delivery - Post-Test

Exploitation - Post-Test

Installation - Post-Test

Command and Control (C2) - Post-Test

Actions on Objectives (Impact) - Post-Test

3.2 Example Containment And Eradication Procedures
A step-by-step breakdown of the immediate response actions taken to isolate the compromised system, remove the phishing payload, and prevent reinfection.
🔹 Containment Strategy Objective: Prevent further attacker activity by isolating compromised systems, terminating malicious processes, and blocking C2 communications.
✔ Step 1: Isolate Affected Host
Use LimaCharlie to isolate the compromised endpoint:
limacharlie isolate --sid <sensor_id_of_bob>
Verify isolation through LimaCharlie console and Splunk network logs.
✔ Step 2: Terminate Malicious Processes
Kill processes associated with the attack (LOLBins and payloads):
limacharlie terminate --sid <sensor_id_of_bob> --process mshta.exe limacharlie terminate --sid <sensor_id_of_bob> --process rundll32.exe limacharlie terminate --sid <sensor_id_of_bob> --process kevin_beacon.exe
✔ Step 3: Block C2 Channels
Apply firewall rules to block outbound traffic to attacker-controlled IPs and ports:
netsh advfirewall firewall add rule name="Block FIN7 C2" dir=out action=block remoteip=10.26.0.9
Use Splunk to verify no active connections:
index=sysmon_logs EventID=3 (DestinationIp="10.26.0.9" OR DestinationPort=443 OR DestinationPort=54321)
🔹 Eradication Strategy Objective: Remove persistence mechanisms, clean the system of malware artifacts, and ensure no residual attacker footholds remain.
✔ Step 1: Remove Malicious Registry Keys & Scheduled Tasks
Remove detected persistence:
# Remove registry run key Remove-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\Run" -Name "AdobeFakeUpdate" -ErrorAction SilentlyContinue # Remove scheduled task if present schtasks /delete /tn "AdobeFakeUpdate" /f
Verify removal:
Get-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\Run" -Name "AdobeFakeUpdate" -ErrorAction SilentlyContinue schtasks /query /tn "AdobeFakeUpdate"
✔ Step 2: Locate & Delete Dropped Files
Search and remove malicious files:
Get-ChildItem -Path C:\Users\Public -Filter "kevin_beacon.*" -Recurse | Remove-Item -Force
✔ Step 3: Conduct a Full System Scan
Use Windows Defender to ensure full malware removal:
Start-MpScan -ScanType FullScan
✔ Step 4: Review PowerShell Execution History
Investigate historical PowerShell commands:
Get-History | Select-String "Invoke-WebRequest"
3.3 Incident Response Playbook Sample
A structured response plan that details predefined actions SOC analysts can take when handling similar phishing incidents in the future.
Title: Endpoint Threat Mitigation Playbook
Purpose: This playbook provides a structured methodology for detecting and mitigating endpoint threats related to FIN7-style attack techniques. It focuses on initial access, execution, persistence, and command & control (C2) activities, leveraging endpoint detection tools such as Sysmon, Splunk, YARA, and LimaCharlie EDR.
▸ Key Playbook Actions
Detect: Use Sysmon and Splunk queries to identify suspicious execution (PowerShell, LOLBins) and persistence mechanisms (registry keys, scheduled tasks).
Analyze: Perform YARA scans on suspicious files and review process and file creation logs to confirm threat presence.
Contain: Isolate the affected endpoint using LimaCharlie and block further malicious execution through Group Policy and process termination.
Eradicate: Remove registry keys, delete malicious files, and clean up scheduled tasks to eliminate persistence.
Restore: Re-enable security controls, audit policies, and generate a comprehensive incident report for documentation and future prevention.
📄 Full Playbook: See Appendix 5.2 – Endpoint Threat Mitigation Playbook
4. Findings & Recommendations
This section summarizes key observations from the assessment, provides security recommendations, and outlines areas for future improvement.
4.1 Findings
A summary of security gaps identified during the attack simulation, as well as improvements in detection and response capabilities.
Detection significantly improved but was still slower than attack execution. Prior to implementing detection rules, payload execution went unnoticed. Post-test enhancements with Sysmon and Splunk allowed detection within 1 minute of execution. However, the attacker achieved a reverse shell within 5 seconds of LNK file execution, highlighting the need for faster detection or pre-execution blocking measures.
Privilege escalation and persistence attempts were effectively mitigated. The Red Team was unable to escalate privileges or establish persistence post-test due to improved detection of registry modifications and scheduled task creations. These detections allowed immediate remediation, preventing attacker foothold.
Threat containment improved with LimaCharlie but was manually triggered. While the SOC successfully contained the compromised host within 5 minutes post-detection, the response was manual. Automated containment workflows could reduce response times further, potentially preventing successful payload execution.
Detection correlation improved but lacked full attack chain visibility. SIEM alerts for different stages (execution, persistence attempts, and C2 communication) were triggered separately. Although detection coverage improved, these events were not automatically correlated into a single incident timeline, requiring manual investigation.
C2 detection improved with targeted network rules. Initial tests failed to detect command-and-control activity. Post-test improvements, including specific rules for known C2 ports and abnormal high-port connections, enabled the SOC to detect and respond to C2 attempts, including protocol switches between HTTPS and TCP.
User action remains a significant initial access risk. Despite detection and containment improvements, the attack’s success relied on a user opening the malicious LNK file. User awareness and phishing simulation programs remain critical to reducing this initial risk vector.
4.2 Recommendations
Actionable security measures that should be implemented to enhance attack detection, incident response efficiency, and overall SOC maturity.
Implement pre-execution blocking measures: Utilize application whitelisting, controlled folder access, and restrict execution of LNK files from email attachments to prevent initial payload execution.
Automate containment workflows: Integrate automated host isolation triggers within the SIEM to reduce containment time to seconds rather than minutes.
Enhance correlation of multi-stage attacks: Develop Splunk correlation searches that link initial access, execution, and C2 events to present a full attack chain view, enabling faster analyst response.
Increase endpoint visibility and hardening: Expand Sysmon configurations to include parent-child process relationships and command-line logging for common LOLBins to catch subtle execution chains.
Conduct regular phishing awareness training: Reduce the likelihood of user-initiated attacks by implementing routine phishing simulations and security awareness programs.
Continuously test and tune detection rules: Regularly validate and refine detection rules to adapt to evolving threat actor techniques, ensuring minimal false positives while maintaining coverage.
Evaluate behavioral-based detection tools: Consider deploying machine-learning-driven EDR solutions that can detect anomalous behavior even before signature-based detections trigger.
4.3 Lessons Learned
A reflection on what worked well, what was initially missed, and how the incident response process can be improved based on the assessment results.
Detection Gaps
Delayed detection of initial payload execution: Although detection improved post-test, the payload still executed before alerts triggered, enabling the attacker to gain a reverse shell within seconds.
Missed early C2 communications: Outbound connections to malicious ports initially evaded detection, highlighting the need for enhanced network telemetry.
Limited event correlation: While individual attack stages were detected, events were not automatically correlated into a single alert, slowing the analyst’s ability to identify the full attack chain.
Incomplete detection of LOLBins abuse: Initial configurations did not flag executions of common living-off-the-land binaries (LOLBins), such as mshta.exe and rundll32.exe, until dedicated detection rules were implemented.
Insufficient persistence detection: Registry-based persistence attempts went unnoticed during the initial phase, requiring more comprehensive registry monitoring.
Response Delays
Manual containment slowed response: Host isolation relied on manual intervention, taking approximately 5 minutes post-detection—too slow to prevent immediate attacker objectives.
Lack of automated incident triage: SOC analysts had to manually investigate and validate alerts, delaying coordinated response actions.
Delayed user notification: No immediate communication was sent to the user of the compromised endpoint, allowing continued interaction with the payload.
4.4 Next Steps
To address the identified gaps and enhance overall security posture, the following prioritized actions are recommended:
Immediate Priorities (1-3 months)
Automate host isolation: Implement SIEM-to-EDR integration to enable automatic host isolation within seconds of detection.
Refine SIEM correlation rules: Develop Splunk correlation searches that consolidate execution, persistence, and C2 events into a single high-confidence alert.
Improve endpoint visibility: Expand Sysmon configurations to capture parent-child process relationships and command-line arguments.
Enhance user awareness: Conduct phishing simulations and awareness training to reduce user-initiated compromises.
Mid-term Priorities (4-6 months)
Deploy application whitelisting: Use tools like AppLocker to prevent unauthorized file executions.
Extend log retention: Increase Splunk and Sysmon log retention to 90 days for better incident investigation and trend analysis.
Improve network monitoring: Enable DNS and firewall logging to detect early-stage C2 traffic.
Long-term Priorities (7-12 months)
Implement network segmentation: Limit attacker movement by isolating critical systems.
Adopt behavioral detection tools: Evaluate machine learning-driven EDR solutions capable of detecting abnormal user and system behaviors.
Conduct regular detection validation: Schedule biannual red team simulations and blue team drills to ensure detection rules remain effective.
➡️ Overall Goal: Enhance detection speed to under 30 seconds, reduce containment times to under 1 minute, and improve SOC response coordination.
5. Appendices
5.1 Incident Response & Containment Frameworks
The following resources provide industry-recognized guidelines for containment, eradication, and incident response. These frameworks align with best practices and can be used to refine detection strategies, automate response workflows, and improve SOC readiness.
🔹 MITRE ATT&CK – Containment Strategies 🔗 https://attack.mitre.org/tactics/TA0040/ Covers containment tactics used to prevent adversary actions from escalating, helping SOC teams prioritize defensive actions.
🔹 NIST Incident Response Guide (SP 800-61 Rev. 2) 🔗 https://csrc.nist.gov/publications/detail/sp/800-61/rev-2/final An official framework for incident handling, including best practices for containment, eradication, and recovery.
🔹 SANS Incident Response Process 🔗 https://www.sans.org/posters/incident-handlers-handbook/ A step-by-step guide for incident handlers, focusing on containment, forensic analysis, and incident resolution.
🔹 Microsoft Security Response Center (MSRC) – Incident Response Playbooks 🔗 https://learn.microsoft.com/en-us/security/compass/incident-response-playbooks Provides structured playbooks for containing phishing, malware, and other security incidents in enterprise environments.
5.2 Playbook - Endpoint Threat Mitigation Playbook
Version: 1.0
Author: TrilloSec Last Updated: 2025-02-20
1️⃣ Overview
Purpose:
This playbook provides a structured methodology for detecting and mitigating endpoint threats related to FIN7-style attack techniques. It focuses on initial access, execution, persistence, and command & control (C2) activities, leveraging endpoint detection tools such as Sysmon, Splunk, YARA, and LimaCharlie EDR.
Scope:
Focused entirely on endpoint threat detection (network detection to be covered in future experiments).
Emphasizes detection and response for techniques including LOLBins abuse, AMSI bypass, persistence mechanisms, and C2 communications.
Security Domains Covered:
Endpoint Detection & Response (EDR) – LimaCharlie
Host-based Logging & Monitoring – Sysmon + Splunk
Threat Hunting – YARA for memory and file scans
Incident Handling – NIST 800-61 guidance for detection, containment, and eradication
2️⃣ Pre-Incident Preparation
Baseline Security Controls:
Control | Status | Notes |
Sysmon Logging | ✅ Enabled | Monitors process creation, registry changes, file events |
LimaCharlie EDR | ✅ Active | Provides process and network event alerts |
Splunk SIEM | ✅ Deployed | Aggregates Sysmon and EDR logs for threat correlation |
Sigma Rule Integration | ✅ In Progress | Sigma-based rules converted for Splunk compatibility |
YARA Threat Hunting | ✅ Available | For file integrity and in-memory scans |
3️⃣ Detection & Investigation Workflow
Step 1: Detect Execution (T1204, T1218)
🔎 1.1 Detect Initial Access (LNK Execution)
index=sysmon_logs EventID=1 Image="*cmd.exe" CommandLine="*powershell*"Rationale: Detects user interaction triggering malicious payloads.
🔎 1.2 Detect LOLBins Execution
index=sysmon_logs EventID=1 (Image="*mshta.exe" OR Image="*rundll32.exe" OR Image="*wmic.exe" OR Image="*regsvr32.exe")Rationale: Identifies abuse of native Windows binaries to execute payloads.
🔎 1.3 Use YARA to Scan for Malicious Scripts
# Transfer suspected file from endpoint
scp blue-edr-bob@10.26.00.105:/C/Users/Public/payload.ps1 /mnt/analysis/
# Scan with YARA
yara -r rules/fin7.yara /mnt/analysis/payload.ps1Step 2: Investigate & Contain
🔎 2.1 Investigate AMSI Bypass Attempts
index=sysmon_logs EventID=1 CommandLine="*amsi.dll*"🔒 2.2 Isolate Compromised Host
limacharlie isolate --sid <sensor_id_of_bob>🛡️ 2.3 Block LOLBins Execution via Group Policy (Remote or On-Host)
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" -Name "EnableLUA" -Value 0Step 3: Investigate Persistence (T1547)
🔎 3.1 Detect File Drops (Beacon Payload)
index=sysmon_logs EventID=11 TargetFilename="*kevin_beacon.*"🔎 3.2 Detect Registry-based Persistence
index=sysmon_logs EventID=13 TargetObject="*Run\\*"🔎 3.3 Investigate Scheduled Tasks
Get-ScheduledTask | Where-Object { $_.RegistrationInfo.Date -gt (Get-Date).AddDays(-1) }Step 4: Eradication & Recovery
🚨 4.1 Terminate Malicious Processes
limacharlie terminate --sid <sensor_id_of_bob> --process mshta.exe
limacharlie terminate --sid <sensor_id_of_bob> --process rundll32.exe🧹 4.2 Remove Malicious Registry Keys
Remove-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\Run" -Name "AdobeFakeUpdate" -ErrorAction SilentlyContinue🗑️ 4.3 Clean Up Scheduled Tasks
schtasks /delete /tn "AdobeFakeUpdate" /f🔄 4.4 Re-enable Security Controls
Set-ItemProperty -Path "HKLM:\Software\Microsoft\Windows\CurrentVersion\Policies\System" -Name "EnableLUA" -Value 1
AuditPol /set /category:"Logon/Logoff" /success:enable /failure:enable📄 4.5 Generate Incident Report
splunk search 'index=sysmon_logs host="blue-edr-bob"' | outputreport --title "FIN7 Detection Report" --format pdf5.3 YARA Rules
Delivery: Detect Malicious Email Attachments and File Drops
rule Delivery_Detect_Malicious_Email_Attachments_and_File_Drops
{
meta:
author = "Your Name"
description = "Detects PowerShell in-memory attacks or dropped executables/DLLs in common directories like Public and Temp."
threat_level = 3
date = "2024-02-22"
strings:
// PowerShell command-line patterns
$iex = "IEX"
$download1 = "DownloadString"
$download2 = "DownloadFile"
$invoke_web = "Invoke-WebRequest"
$invoke_expr = "Invoke-Expression"
$curl = "curl"
$wget = "wget"
// File drop paths
$public_path = "\\Users\\Public\\"
$exe_ext = ".exe"
$dll_ext = ".dll"
condition:
(
any of ($iex, $download1, $download2, $invoke_web, $invoke_expr, $curl, $wget)
and filesize < 2MB // Optional size filter for scripts
)
or
(
( $public_path )
and ( $exe_ext or $dll_ext )
)
}Exploitation: Detect AMSI Bypass Attempts
rule AMSI_Bypass_Attempt
{
meta:
description = "Detects AMSI bypass attempts via PowerShell commands or process memory modifications targeting amsi.dll"
author = "TrilloSec"
date = "2025-02-22"
mitre_techniques = "T1059.001, T1562.001, T1055"
strings:
// PowerShell command-line indicators
$amsi = "amsi" nocase
$bypass = "bypass" nocase
$reflection = "Reflection.Assembly" nocase
$add_type = "Add-Type" nocase
$invoke_expression = "Invoke-Expression" nocase
$new_object = "New-Object System.Net.WebClient" nocase
$iex = "IEX" nocase
$downloadstring = "DownloadString" nocase
// Process memory modification indicators
$virtual_protect = "VirtualProtect" nocase
$write_process_memory = "WriteProcessMemory" nocase
$amsi_dll = "amsi.dll" nocase
condition:
any of ($amsi, $bypass, $reflection, $add_type, $invoke_expression, $new_object, $iex, $downloadstring)
or any of ($virtual_protect, $write_process_memory, $amsi_dll)
}Installation: Detect Persistence via Registry and Scheduled Tasks
rule Persistence_Registry_RunKeys_and_Scheduled_Tasks
{
meta:
description = "Detects persistence via modifications to Run/RunOnce registry keys and the creation of scheduled tasks."
author = "TrilloSec"
date = "2025-02-22"
mitre_techniques = "T1547.001, T1053.005"
threat_level = 2
strings:
// Registry keys for persistence
$run_key = "\\Software\\Microsoft\\Windows\\CurrentVersion\\Run"
$runonce_key = "\\Software\\Microsoft\\Windows\\CurrentVersion\\RunOnce"
// Scheduled task creation commands
$schtasks_cmd = "schtasks" nocase
condition:
any of ($run_key, $runonce_key)
or $schtasks_cmd
}C2: Detect Suspicious Network-Based C2 Activity
rule C2_Detect_Suspicious_Network_Connections
{
meta:
description = "Detects likely C2 activity via outbound connections to known C2 ports or uncommon high ports."
author = "TrilloSec"
date = "2025-02-22"
mitre_techniques = "T1071.001, T1071.004"
threat_level = 1
strings:
// Known C2 ports
$port_4444 = ":4444"
$port_1337 = ":1337"
$port_8080 = ":8080"
$port_9001 = ":9001"
// Common excluded ports (for context, not matched directly)
$excluded_80 = ":80"
$excluded_443 = ":443"
$excluded_8443 = ":8443"
condition:
// Matches known C2 ports
any of ($port_4444, $port_1337, $port_8080, $port_9001)
or
// Matches any port above 1024 excluding common ports
(
for any i in (1025..65535) : (
(uint16(0) i) and
not any of ($excluded_80, $excluded_443, $excluded_8443)
)
)
}Actions on Objectives: Detect Forced System Impact Demonstration
rule Detect_Forced_Browser_Execution
{
meta:
description = "Detects suspicious forced browser launches, like rickrolling or redirect attacks."
author = "TrilloSec"
date = "2025-02-22"
mitre_techniques = "T1491.001"
threat_level = 3
strings:
$msedge_process = "msedge.exe" nocase
condition:
$msedge_process
}5.4 LimaCharlie EDR Rules
Delivery: Detect Malicious Email Attachments and File Drops
op: or
events:
- NEW_PROCESS
- FILE_WRITTEN
rules:
- op: and
rules:
- op: contains
path: event/PROCESS_CMD_LINE
value: IEX
- op: matches
path: event/PROCESS_CMD_LINE
re: ".*(DownloadString|DownloadFile|Invoke\\-WebRequest|Invoke\\-Expression|curl|wget).*"
- op: matches
path: event/FILE_PATH
re: ".*(\\\\Users\\\\Public\\\\).*(\\.exe|\\.dll)$"
response:
- action: report
name: "Delivery: Detect Malicious Email Attachments and File Drops"
priority: 3
description: "Detects delivery techniques via PowerShell in-memory attacks or dropped executables/DLLs in common directories like Public and Temp."Exploitation: Detect AMSI Bypass Attempts
op: or
events:
- NEW_PROCESS
- PROCESS_MEMORY_MODIFICATION
rules:
- op: and
rules:
- op: is
path: event/PROCESS_NAME
value: powershell.exe
- op: matches
path: event/PROCESS_CMD_LINE
re: ".*(amsi|bypass|Reflection\\.Assembly|Add-Type|[Ii]nvoke-Expression).*"
- op: and
rules:
- op: is
path: event/PROCESS_NAME
value: powershell.exe
- op: matches
path: event/PROCESS_CMD_LINE
re: ".*(New-Object\\s+System\\.Net\\.WebClient|IEX|DownloadString).*"
- op: and
rules:
- op: is
path: event/EVENT_TYPE
value: PROCESS_MEMORY_MODIFICATION
- op: contains
path: event/PROCESS_NAME
value: powershell.exe
- op: matches
path: event/PROCESS_CMD_LINE
re: ".*(VirtualProtect|WriteProcessMemory|amsi.dll).*"
response:
- action: report
name: "Detection: AMSI Bypass Attempt"
priority: 1
description: "Detects AMSI bypass attempts via PowerShell commands or process memory modifications targeting amsi.dll."Installation: Detect Persistence via Registry and Scheduled Tasks
op: or
events:
- REGISTRY_KEY_WRITTEN
- NEW_PROCESS
rules:
- op: and
rules:
- op: is
path: event/EVENT_TYPE
value: REGISTRY_KEY_WRITTEN
- op: contains
path: event/REG_KEY
value: "\\Software\\Microsoft\\Windows\\CurrentVersion\\Run"
- op: and
rules:
- op: is
path: event/EVENT_TYPE
value: REGISTRY_KEY_WRITTEN
- op: contains
path: event/REG_KEY
value: "\\Software\\Microsoft\\Windows\\CurrentVersion\\RunOnce"
- op: and
rules:
- op: is
path: event/EVENT_TYPE
value: NEW_PROCESS
- op: contains
path: event/PROCESS_CMD_LINE
value: schtasks
response:
- action: report
name: "Installation: Detect Persistence via Registry and Scheduled Tasks"
priority: 2
description: "Detects common persistence methods via modifications to Run/RunOnce registry keys and the creation of scheduled tasks."C2: Detect Suspicious Network-Based C2 Activity
op: or
events:
- NETWORK_CONNECT
rules:
- op: and
rules:
- op: is
path: event/EVENT_TYPE
value: NETWORK_CONNECT
- op: matches
path: event/REMOTE_PORT
re: "^(4444|1337|8080|9001)$"
- op: and
rules:
- op: is
path: event/EVENT_TYPE
value: NETWORK_CONNECT
- op: matches
path: event/REMOTE_PORT
re: "^([1-9][0-9]{3,5}|[2-9][0-9]{2,4}|102[5-9]|10[3-9][0-9]|1[1-9][0-9]{2}|[2-9][0-9]{3,4})$" # Matches ports above 1024 excluding 80, 443, 8443
response:
- action: report
name: "C2: Detect Suspicious Network-Based C2 Activity"
priority: 1
description: "Detects likely C2 activity via outbound connections to known C2 ports or uncommon high ports."Actions on Objectives: Detect Forced System Impact Demonstration
event: NEW_PROCESS
op: contains
path: event/PROCESS_NAME
value: msedge.exe
response:
- action: report
name: "Detected Force Browser Execution"
priority: 3
description: "Detects suspicious forced browser launches, like rickrolling or redirect attacks."TL;DR
Blue Team improved endpoint threat detection with:
✅ 100% detection of LOLBins and AMSI bypass attempts.
✅ <1 min detection time for C2 activity and payload execution.
✅ 5 min containment post-detection, reducing attacker dwell time.
✅ $58K estimated financial risk reduction per incident.
Download PDF:
Other Reports in This Project
✔ Red Team: Simulated a FIN7-inspired endpoint attack using LNK payloads, PowerShell execution, and C2 channels to test detection gaps.
✔ Blue Team: Developed Sysmon, Splunk, and LimaCharlie EDR detection rules, reducing detection time to under 1 minute and containment to 5 minutes.
✔ Purple Team: Quantified risk reduction of $58K per incident, aligned defenses with NIST 800-53, ISO 27001, and improved SOC response efficiency.
✔ Setup Guide: Configured attack and defense environments with Gophish, Metasploit, Sysmon, and Splunk for consistent, repeatable testing.


