05-Cloud-Security (Microsoft 365 & Azure)
- TrilloSec

- Mar 22
- 5 min read
Updated: Mar 24

Microsoft 365 & Azure Security Lab – Hardening & Threat Detection
1. Project Overview
Objective:
This project focuses on Microsoft 365 and Azure security administration, including:
Configuring security features (MFA, Defender for Office 365, Entra ID Security Defaults)
Generating and analyzing security logs (failed logins, phishing attempts, impossible travel detections)
Setting up Azure Security monitoring (Azure Sentinel, Conditional Access Policies, Microsoft Defender)
Simulating cyber threats to assess detection capabilities
This hands-on lab strengthens SOC Analyst skills in Microsoft environments and demonstrates my ability to secure cloud-based enterprise systems.
2. Microsoft 365 Security Administration
2.1 Setting Up Microsoft 365 E5 Trial
✅ Steps Taken:
Registered for Microsoft 365 E5 trial
Created test users:
Configured security policies:
Enabled Multi-Factor Authentication (MFA)
Enabled Microsoft Defender for Office 365
Activated Entra ID Security Defaults
📸 Screenshots:
Enabled Multi-Factor Authentication (MFA)

Enabled Microsoft Defender for Office 365

Activated Entra ID (Formerly Azure AD) Security Defaults

2.2 Generating & Analyzing Security Logs
✅ Simulated Security Events:
Simulated a failed MFA login attempt to trigger security logs
Sent a phishing email to test Defender for Office 365 protection
Logged into Office 365 from different locations using a VPN to trigger impossible travel alerts
Failed MFA logins
Objective: Fail MFA logins to trigger Entra ID security alerts
Attack Simulation: Attempted to log into https://office.com with wrong password 3 times. Tried to log in a fourth time using correct "stolen" credentials but MFA (MS Authenticator App) denied access.

Detection & Analysis: Entra ID Sign-In Logs showing 3 failed password attempts (error 50126) and a failed MFA attempt (error 500121).

Phishing attack simulation
Objective: Launch a phishing attack simulation using Defender for Office 365
Attack Simulation: Microsoft 365 includes a built-in phishing simulation tool under Microsoft Defender for Office 365 Plan 2.

Detection & Analysis: A real-time report captured the interaction of User1 being phished. Each step was recorded from initially reading the message, to clicking the link, and supplying their login credentials.
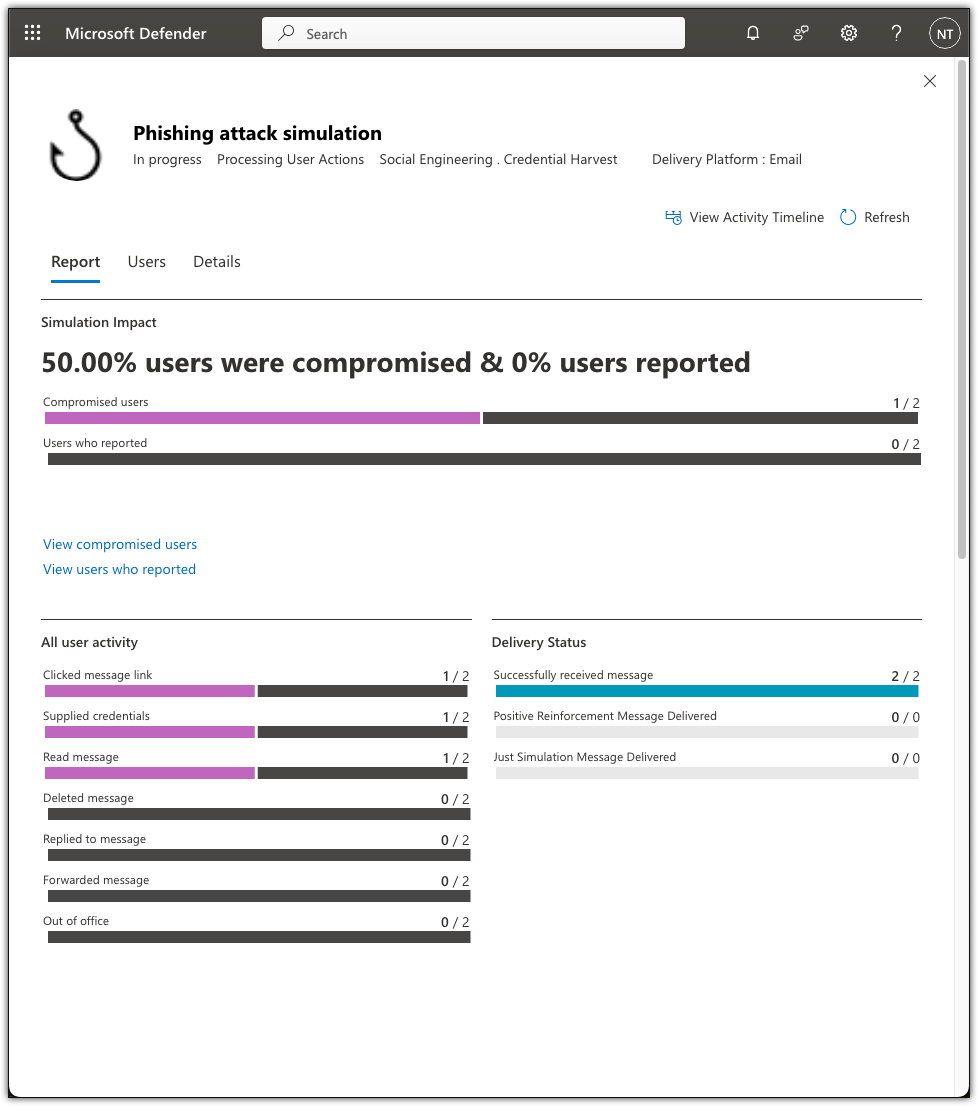
Impossible Travel alert
Objective: Generate and an Impossible Travel alert by logging in from two different locations with a VPN.
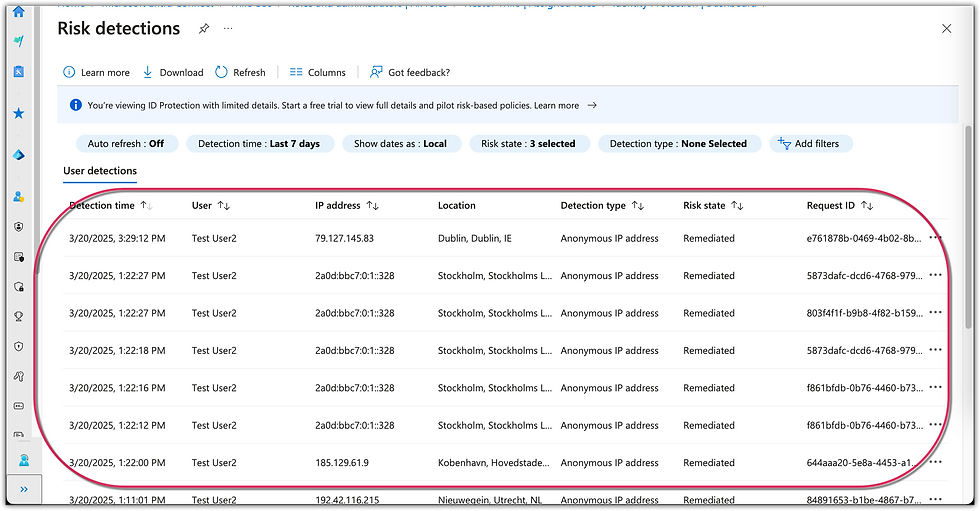
Attack Simulation: The Impossible Travel detection identifies scenarios where a user appears to have signed in from two distant locations in a timeframe too short for physical travel, indicating a potential security risk. In order to function effectively, the detection algorithm requires 14 days or 10 sig-ins of activity history to establish a baseline. Therefore, I logged in as User2 at https://myapps.microsoft.com more than 10 times with no VPN using Safari browser. After setting this baseline, I used a VPN to log in from wildly distant geographical locations such as California, Belarus, Australia, and Ireland within the span of a few minutes.

Detection & Analysis: Detection of impossible travel events is not real-time. The "Risky Sign-Ins" log was set to auto refresh every 5 minutes. After about 15 minutes, the first impossible travel event was logged.

The remaining simulated attacks appeared under the "Risk Detections" section.
3. Azure Security & Threat Detection
3.1 Setting Up Azure Security Monitoring
✅ Steps Taken:
Enabled Microsoft Defender for Cloud (Formerly Azure Security Center)
Configured Defender for Identity (MDI) (Formerly Azure ATP) to monitor Entra ID events
Deployed Azure Sentinel (SIEM) and ingested logs
📸 Screenshots:
Enabled Microsoft Defender for Cloud

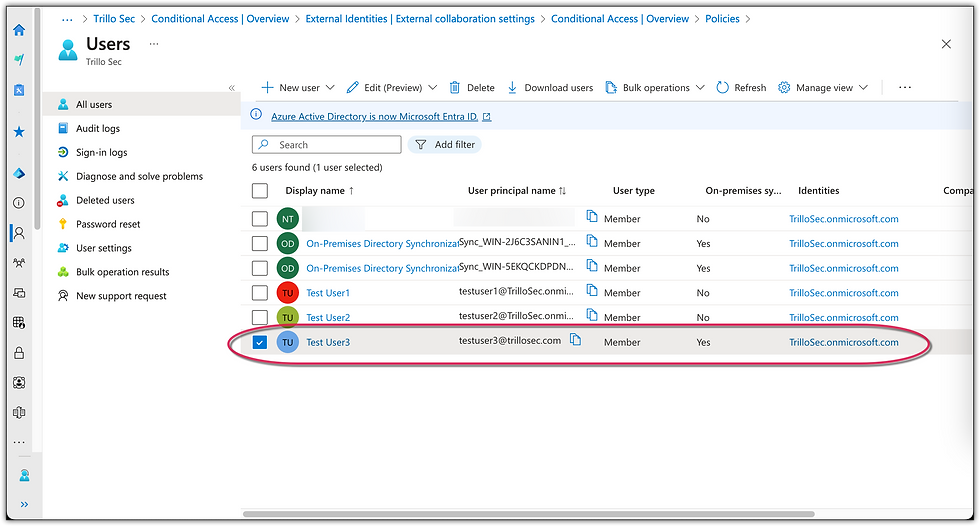
Configured Defender for Identity (MDI) to monitor Entra ID events for an on-premises Active Directory Domain Controller. First, I set up a new Windows Server 2025 as a AD DC and installed Entra Synchronization connector. After creating a local User3, i was able to synch with the rest of the accounts online.
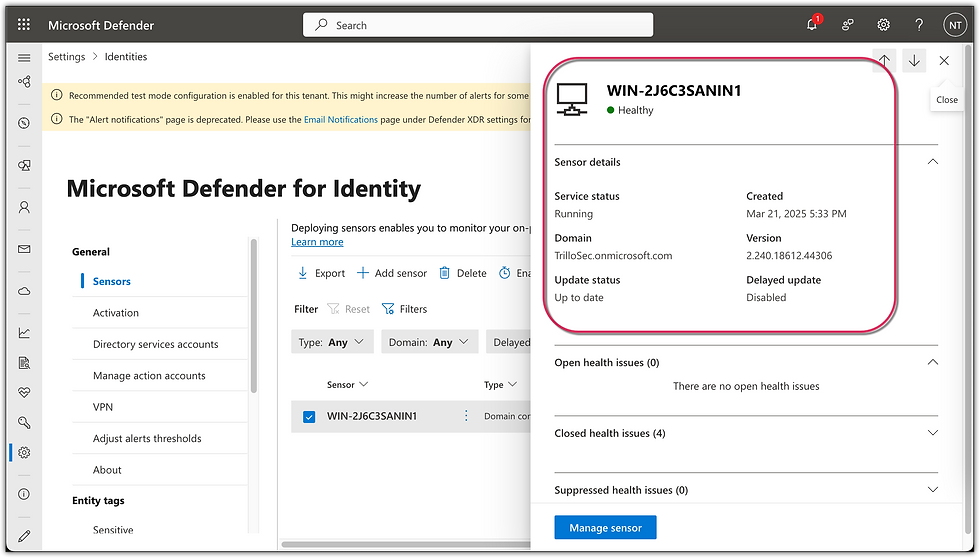
I was then able to deploy a sensor for Microsoft Defender for Identity onto the on-premise AD DC server.
Deployed Azure Sentinel (SIEM) and installed six (6) data connectors for capturing events.

Confirmed successful ingestion of events into logs.

3.2 Simulating & Detecting Threats
✅ Threat Scenarios Simulated:
Added User to Sensitive Group: Add a regular user to Domain Admin group to generate a security alert.
Entra ID Conditional Access Policy: Created a rule to block access from non-corporate locations.
Security Log Review in Sentinel: Analyzed failed login attempts, and unusual activities.
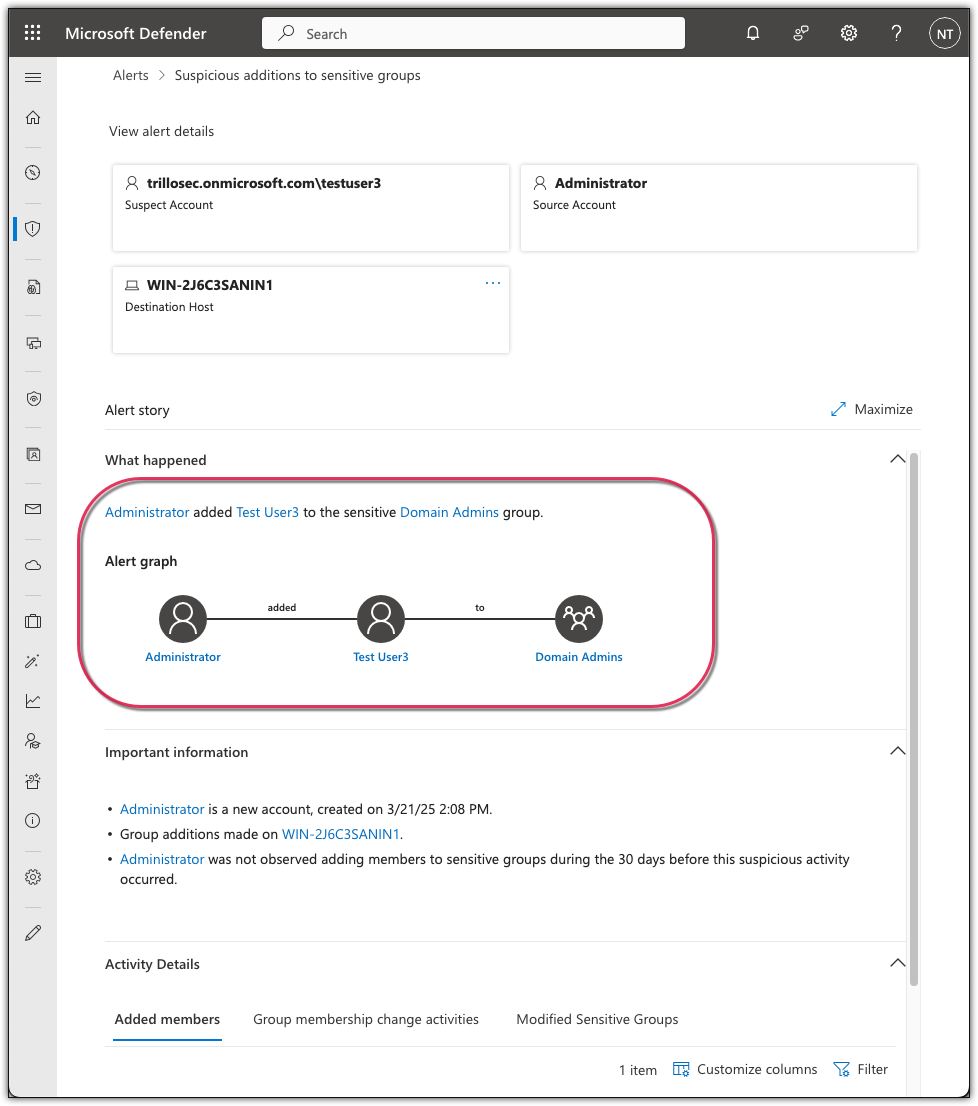
Added User to Sensitive Group
Objective: Add a regular user to Domain Admin group to generate a security alert.
Attack Simulation: On the Domain Controller, added "Test User3" to group "Domain Admins".

Detection & Analysis: The above action triggered a "Suspicious additions to sensitive groups" alert.
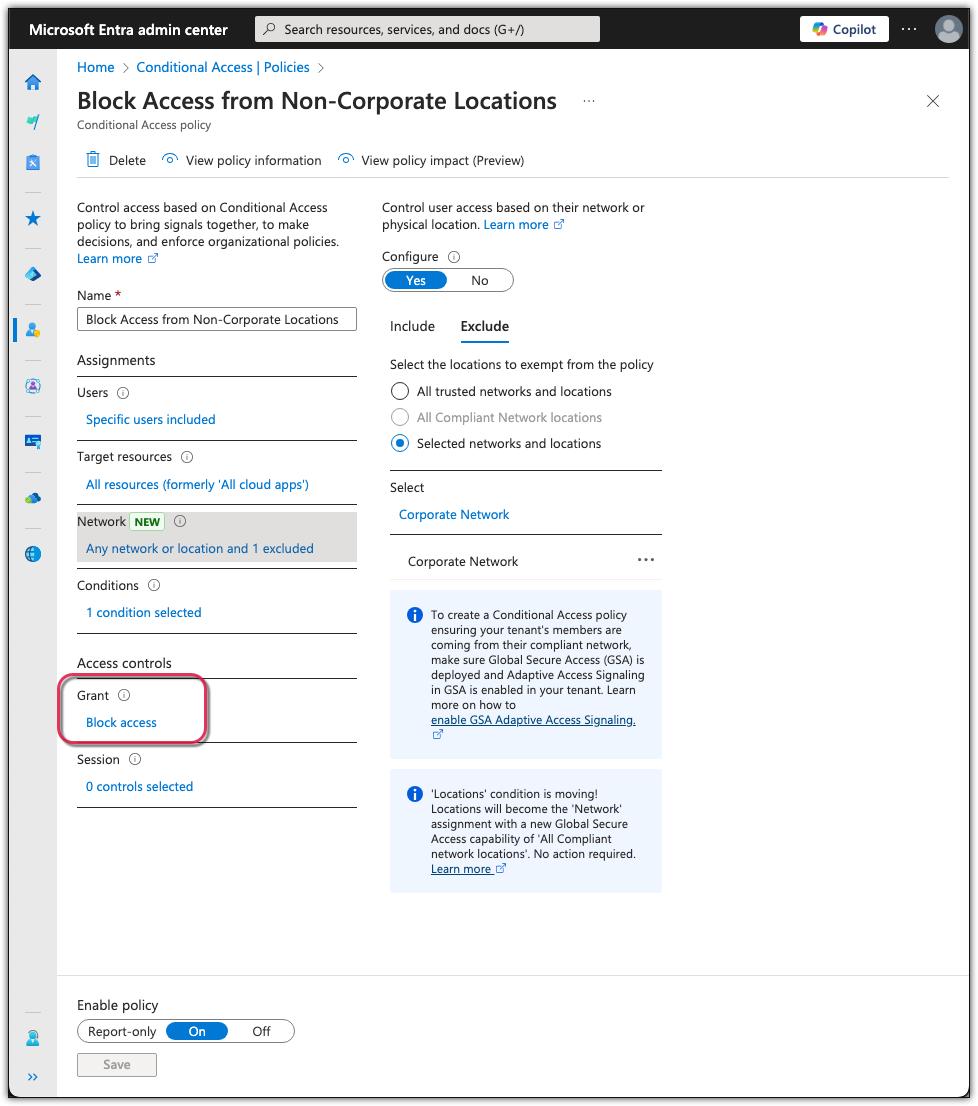
Entra ID Conditional Access Policy
Objective: Create a rule to block access from non-corporate locations.
Attack Simulation: In Entra Admin Center, defined "Corporate Network" as being in anywhere in the United States. Then created a Conditional Access Policy to block access from non-corporate locations.
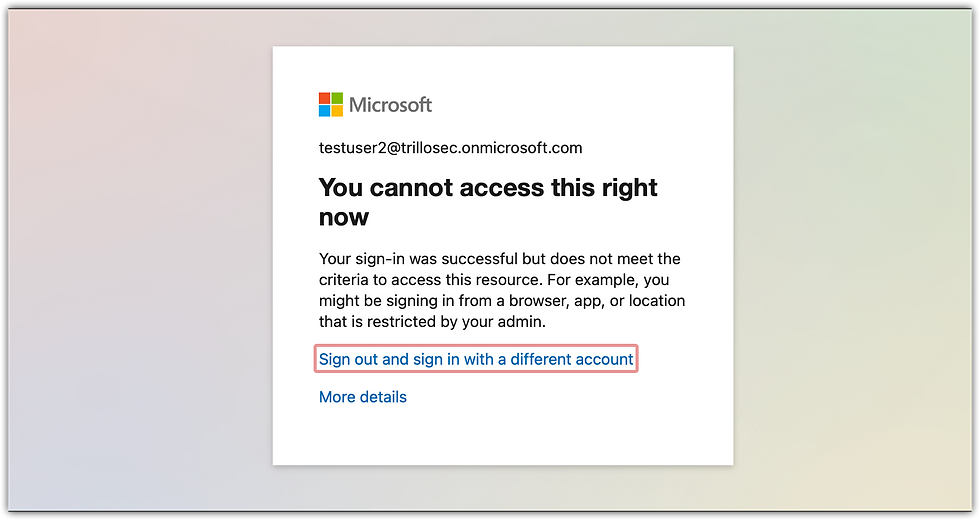
To test the effectiveness of an Entra ID Conditional Access Policy configured to block access from non-corporate locations, I attempted to sign in as testuser2@trillosec.onmicrosoft.com from an external network via myapps.microsoft.com. A VPN was used to attempt logging in from the United Kingdom as User2. Initial login without the VPN was successful. Subsequent login attempt via the VPN resulted in the following screen.
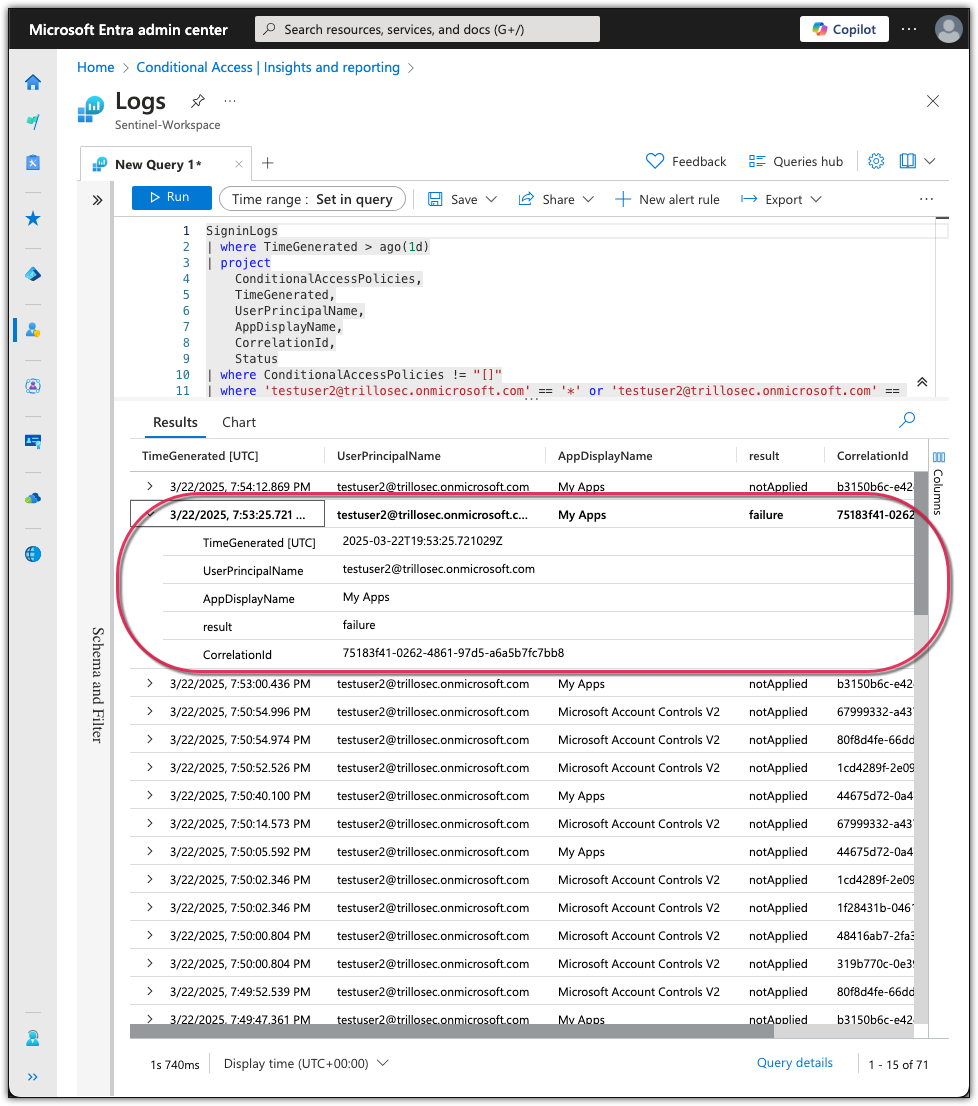
Detection & Analysis: The screenshot shows the Sign-in Logs from Microsoft Sentinel, filtered to surface only events where Conditional Access policies were evaluated. The entry highlighted confirms that access to "My Apps" was denied, with the result marked as "failure" and ConditionalAccessPolicies not applied, indicating enforcement of the policy and successful prevention of unauthorized access.
Security Log Review in Sentinel
Objective: Analyze failed login attempts, and unusual activities.
Attack Simulation 1 of 2: For failed login attempts, I attempted multiple incorrect password logins in rapid succession using an incognito browser.
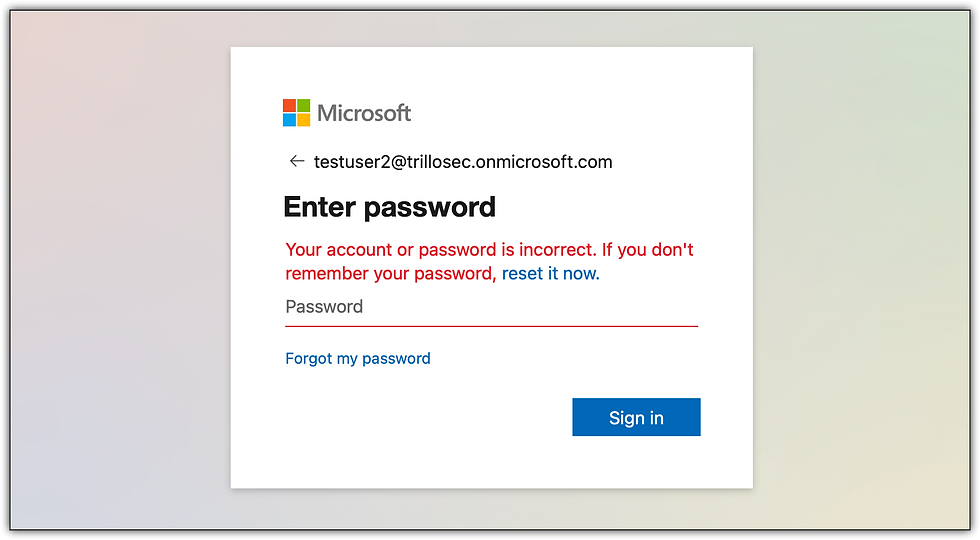
Detection & Analysis 1 of 2: This screenshot shows failed login attempts for usernames with more than 3 failures in a 5-minute window indicative of a possible brute-force attack.

Attack Simulation 2 of 2: For Unusual Activity, I used a VPN to log as testuser2@trillosec.onmicrosoft.com from random location within the US via myapps.microsoft.com using a VPN.
Detection & Analysis 2 of 2: Using Microsoft Defender’s advanced hunting capability, I ran a custom KQL query against SigninLogs to identify potentially suspicious sign-ins from multiple locations. The results for testuser2@trillosec.onmicrosoft.com show login activity from geographically distant cities — including Honolulu, Washington, Dallas, and Castlereagh — within a short timeframe.

4. Key Findings & Lessons Learned
4.1 Security Enhancements Identified
Enabling MFA significantly reduces unauthorized access risks.
Microsoft Defender for Office 365 is effective in blocking phishing attempts.
Azure Sentinel logs provide powerful detection capabilities for anomalous activity.
4.2 Improvements for Future Labs
Investigate Power Automate for Security Response Automation
Explore deeper Azure Sentinel KQL queries for SIEM monitoring
5. Conclusion & Next Steps
This project improved my hands-on experience with Microsoft 365 and Azure security tools, providing practical skills for SOC operations in cloud environments. Moving forward, I will:
Continue exploring Microsoft Defender for Endpoint integration
Prepare for the Microsoft 365 Fundamentals (MS-900) certification
Expand my skills in Azure Security Center and SIEM tuning
TL;DR
Simulated identity-based attacks in Microsoft 365 and Azure environments, including MFA failures, phishing, and impossible travel. Enabled Defender for Identity, Defender for Office 365, Conditional Access, and Azure Sentinel to detect threats. Successfully triggered alerts for suspicious admin elevation, blocked non-corporate logins via Conditional Access, and used KQL to identify brute-force and anomalous login activity across geographies.
Download PDF:


