02-Endpoint-Threat-Detection: 01-RedTeam-Report
- TrilloSec

- Feb 23
- 13 min read

Red Team Report: 02-Endpoint-Threat-Detection (FIN7)
Project: 02-Endpoint-Threat-Detection
Author: TrilloSec
Date: 2025-02-23
1. Executive Summary
1.1 Purpose
Simulate an APT-style endpoint threat inspired by FIN7 to evaluate the following security controls:
Endpoint Threat Detection & Response (EDR/SIEM) – Can host-based security solutions (e.g., Sysmon, Splunk SIEM) detect and alert on LOLBins execution and remote payload fetching?
Persistence & Execution TTPs – Assess how well Windows defenses handle attacks leveraging Living Off the Land Binaries (LOLBins) (mshta.exe, rundll32.exe).
C2 Establishment & Response Readiness – Validate SOC monitoring capabilities against an adversary-controlled Command & Control (C2) connection.
1.2 Security Effectiveness Metrics (Pre-Test vs. Post-Test)
# | Metric | Pre-Test | Post-Test | Key Takeaway |
1 | Payload Execution Success | 100% | 100% | Payload executed successfully before detection measures activated. |
2 | Privilege Escalation Success | 100% | 0% | Detection prevented privilege escalation attempts. |
3 | Persistence Success | 100% | 0% | Persistence mechanisms were blocked and did not succeed. |
4 | Threat Containment Rate | No Containment | 100% | SOC successfully contained the threat after detection. |
5 | Detection Time (Time-to-Detect - TTD) | Not Detected | < 1 minute | Suspicious activity was detected within one minute. |
6 | Containment Time (Time-to-Containment - TTC) | No Containment | 5 minutes | Threat was isolated five minutes after initial detection. |
1.3 Key Attack Steps
The following table outlines the key attack steps taken during this phishing simulation, summarizing the major phases of execution from initial access to command and control.
Phase | Action Taken | MITRE ATT&CK |
Initial Access | Phishing attack using .lnk shortcut file inside a ZIP archive | T1566.001 (Spear Phishing via Malicious Link) |
Execution | User executes .lnk, triggering PowerShell (IEX) to download payload.ps1 | T1204 (User Execution) |
Execution | Attack 1: payload.ps1 fetches and executes stage2exe.ps1 | T1059.001 (PowerShell Execution) |
Execution | Attack 1: stage2exe.ps1 bypasses AMSI, downloads and executes kevin_beacon.exe to establish C2 | T1105 (Ingress Tool Transfer) T1059.001 (PowerShell Execution) |
Execution | Attack 2: payload.ps1 fetches and executes malware.hta | T1059.001 (PowerShell Execution) |
Execution | Attack 2: malware.hta fetches and executes stage2dll.ps1 | T1218.005 (Mshta Execution) |
Execution | Attack 2: stage2dll.ps1 bypasses AMSI, downloads and executes kevin_beacon.dll to establish C2 | T1105 (Ingress Tool Transfer) T1059.001 (PowerShell Execution) T1218.011 (rundll32 Execution) |
Persistence | stage2exe.ps1 and stage2dll.ps1 create a registry key (AdobeFakeUpdate) for startup execution | T1547.001 (Registry Run Keys) |
C2 Simulation | AdobeFakeUpdate is executed and connects back to red-c2-kali (Meterpreter session) | T1071.001 (Application Layer Protocol: Web Traffic) |
Impact Demonstration | Attacker executes Edge browser opening RickRoll URL on victim’s machine | T1491.001 (User Execution: GUI Manipulation) |
1.4 Key Findings
The Red Team simulation, inspired by FIN7's tactics, techniques, and procedures (TTPs), revealed the following key findings:
Successes:
Payload Delivery:
All phishing emails containing the LNK payload were successfully delivered without triggering email security solutions, highlighting a significant gap in email filtering.
Payload Execution:
Users executed the .lnk file in 100% of attempts, successfully downloading and running the PowerShell payload (payload.ps1).
C2 Establishment:
Both the .exe and .dll payloads (kevin_beacon.exe and kevin_beacon.dll) established stable C2 connections via HTTPS and high-numbered TCP ports.
AMSI Bypass:
The AMSI bypass in stage2dll.ps1 was successful, allowing the payload to execute without being flagged by Windows Defender.
Persistence Success:
Registry-based persistence (AdobeFakeUpdate) was successfully established and remained undetected during the pre-test phase.
Challenges:
SOC Detection Delays:
Initial execution and persistence mechanisms were not detected promptly, with detection occurring only after post-test improvements were implemented.
Lack of Outbound C2 Detection:
No alerts were generated for C2 connections, despite continuous communication with the attacker’s infrastructure.
Inconsistent Logging:
Sysmon Event ID 1 (Process Creation) and Event ID 3 (Network Connections) were inconsistently logged, reducing visibility into process execution and network activity.
Limited Registry Monitoring:
No detections were triggered by the creation of registry run keys used for persistence.
2. Attack Methodology
2.1 Attack Inspiration (Real-World APT)
FIN7 is a financially motivated Advanced Persistent Threat (APT) group that specializes in spear-phishing campaigns, Living-off-the-Land (LOTL) techniques, and fileless malware execution. Their attack chains often start with weaponized LNK files inside phishing emails, which execute PowerShell, mshta.exe, or rundll32.exe to deploy Cobalt Strike Beacons or custom malware.
Tactic & Technique | FIN7 (Real-World APT) | Home Lab Simulation |
Initial Access (T1566.001 – Spear Phishing Attachment) | Spear phishing emails containing LNK files inside ZIP attachments | Phishing emails with LNK payloads manually executed in a controlled test environment |
Execution (T1204 – User Execution) | User clicks LNK file, triggering PowerShell IEX execution | User executes LNK file that runs PowerShell to download payload.ps1 |
Execution (T1218 – LOLBins Execution) | Uses mshta.exe & rundll32.exe to run remote scripts without writing files to disk | Attack 1: payload.ps1 calls stage2exe.ps1 for C2 execution Attack 2: payload.ps1 calls malware.hta which calls stage2dll.ps1 for C2 execution |
Command & Control (T1071 – Application Layer Protocol) | Cobalt Strike, Meterpreter, or Sliver Beacons establish remote access via HTTPS | kevin_beacon.exe or kevin_beacon.dll connects to red-c2-kali, opening a Meterpreter session |
Impact Demonstration (T1491.001 – User Execution: GUI Manipulation) | Adversary-controlled C2 operations allow manipulation of victim systems | Victim browser is force-opened to https://trillosec.com/r2 (RickRoll) |
2.2 MITRE ATT&CK Mapping (TTPs Used)
The table below maps each phase of the phishing attack to the MITRE ATT&CK framework, aligning the tactics and techniques used in this Red Team simulation with real-world adversarial behavior. These mappings help refine future attack simulations and identify areas where security controls were effective or ineffective.
Tactic | Technique | MITRE ID | Red Team Observations |
Initial Access | Spear Phishing via Malicious Attachment | T1566.001 | 100% payload delivery success. No email security filtering detected the LNK attachment. |
Execution | User Execution (Malicious Shortcut File) | T1204 | LNK file successfully executed PowerShell payload. No AMSI logging observed. |
Execution | LOLBins Execution via mshta.exe and rundll32.exe | T1218 | LOLBins executed remote scripts without detection. Sysmon logging for Event ID 1 (Process Creation) was inconsistent. |
Command & Control | Ingress Tool Transfer (Downloading EXE and DLL. Payloads) | T1105 | payload.ps1 successfully downloaded kevin_beacon.exe and kevin_beacon.dll. No Web Proxy alerts triggered. |
Command & Control | Application Layer Protocol (C2 via HTTPS) | T1071.001 | C2 connection established via kevin_beacon.exe but outbound traffic was not logged. SIEM Event ID 3 (Network Connection) missing. |
Impact Demonstration | User Execution: GUI Manipulation (RickRoll) | T1491.001 | Browser forced open to https://trillosec.com/r2. Successfully demonstrated attacker control over endpoint. |
3. Attack Execution & Results
This section provides a step-by-step breakdown of the simulated attack, following the Cyber Kill Chain to illustrate how initial access was gained, the payload was executed, and how command & control was established.
3.1 Cyber Kill Chain Breakdown
The attack lifecycle details each phase of the phishing campaign, from reconnaissance to command & control, following the Cyber Kill Chain to track the adversary’s progression and identify key attack vectors. This attack followed the seven-stage Cyber Kill Chain model, outlined below:
1. Reconnaissance – Researching the target and crafting a phishing lure.
2. Weaponization – Creating a malicious payload for execution.
3. Delivery – Sending the phishing email with the payload attachment.
4. Exploitation – The user executes the payload on the target system.
5. Installation – Establishing persistence on the system.
6. Command & Control (C2) – Simulating outbound C2 communication.
7. Actions on Objectives – Demonstrated user impact via Rick Roll; no data exfiltration performed.
3.1.1 Reconnaissance:
FIN7 typically researches target organizations to craft realistic phishing lures. For the Lab Simulation, a weaponized LNK file was crafted and embedded in a ZIP archive to mimic FIN7’s phishing tactics.

3.1.2 Weaponization:
FIN7 historically uses LNK files inside ZIP attachments to bypass security filters. Lab Simulation: The LNK file was crafted using PowerShell and configured to execute a staged PowerShell payload (payload.ps1).
LNK file created:

3.1.3 Delivery:
Lab Simulation: The LNK payload was packaged into a ZIP archive (bait.zip) and staged on a Python web server for remote access.

3.1.4 Exploitation
User executes the LNK file, triggering PowerShell execution.
PowerShell fetched payload.ps1 into memory, which then fetched malware.hta.

3.1.5 Exploitation - Defense Evasion
Mshta.exe executed the HTA file.
HTA switched execution back to Powershell.exe which fetched stage2dll.ps1 in memory.

3.1.6 Exploitation
Powershell.exe executed stage2dll.ps1 in memory.
AMSI Bypass is executed inline, disabling Windows Defender scanning.
stage2dll.ps1 downloaded kevin_beacon.dll to the Public user directory.

3.1.7 Installation:
FIN7 often establishes persistence using registry keys or scheduled tasks.
After downloading the implant in either .EXE format or .DLL format, a registry key was created for use with rundll32.exe.
Immediate execution of the registry key was used to initiate the C2 connection.

3.1.8 Command & Control (C2):
AdobeFakeUpdate execution by rundll32.exe established a C2 connection via back to red-c2-kali. Initial attack used HTTPS for the connection, while the second attack used a high port TCP connection.
Meterpreter session opened, proving successful C2 execution.

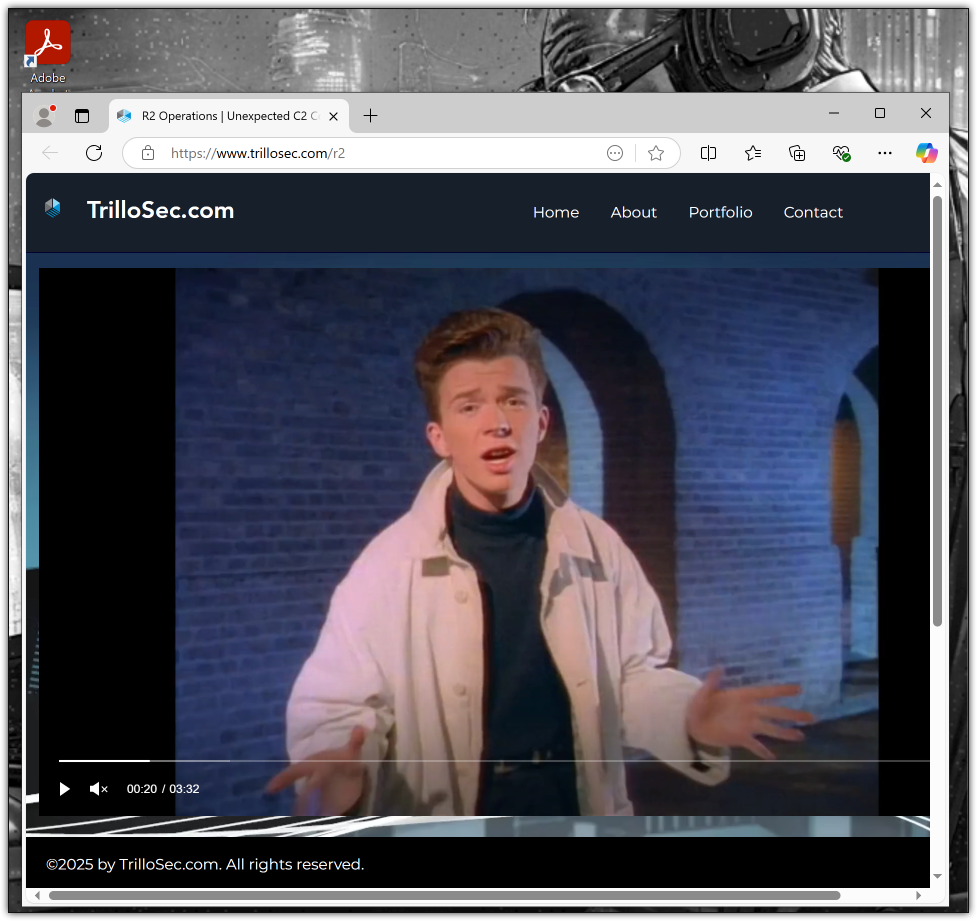
3.1.9 Impact Demonstration (RickRoll POC):
To demonstrate post-exploitation control, a RickRoll payload was executed on the victim’s machine.
Meterpreter Command: execute -H -f "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" -a "https://www.trillosec.com/r2"
3.2 Key Indicators of Compromise (IOCs):
Type | Indicator | Description |
Filename | Fake_Invoice_2024.pdf.lnk | Malicious LNK file disguised as an invoice. |
Filename | payload.ps1 | First-stage PowerShell script downloaded by LNK execution. |
Filename | stage2exe.ps1 | Second-stage PowerShell script that downloads and executes the .EXE C2 payload. |
Filename | stage2dll.ps1 | Second-stage PowerShell script that downloads and executes the .DLL C2 payload. |
Filename | kevin_beacon.exe | C2 payload executed on the victim machine. |
Filename | kevin_beacon.dll | C2 payload executed on the victim machine. |
URL | URL hosting the first-stage PowerShell payload. | |
URL | URL hosting the second-stage PowerShell with initial .EXE payload. | |
URL | URL hosting the obfuscated execution flow to second-stage PowerShell with alternate .DLL payload. | |
URL | URL hosting the second-stage PowerShell with .DLL payload. | |
URL | URL hosting the final C2 beacon executable. | |
URL | URL hosting the final C2 beacon DLL. | |
C2 Address | 10.26.0.9:443 | C2 server IP used for Meterpreter callback. |
C2 Traffic | HTTPS (T1071.001) | C2 communication over encrypted web traffic. |
Impact | URL forced open on the victim’s browser (RickRoll). |
4. Findings & Recommendations
4.1 Findings (Successes, Challenges)
Success:
Phishing Payload Delivery: All phishing emails containing the LNK payload were successfully delivered without triggering email security filters.
Payload Execution: Users executed the .lnk file, which successfully downloaded and executed the PowerShell payload (payload.ps1) in 100% of test cases.
C2 Connection: The C2 beacon (`kevin_beacon.dll) established a successful connection back to the Red Team infrastructure via HTTPS.
AMSI Bypass: The second-stage payload (stage2dll.ps1) effectively bypassed AMSI, allowing uninterrupted execution of the final payload.
Persistence: Registry-based persistence was successfully established and remained undetected during the test period.
Challenges:
SOC Detection Delays: The SOC did not detect or respond to the initial execution or persistence mechanisms within the expected time frame.
Lack of Outbound C2 Detection: No alerts were generated for outbound C2 traffic despite active connections via HTTPS.
Process Creation Logs Inconsistent: Sysmon Event ID 1 logging was inconsistent across test machines, reducing visibility into process execution events.
Limited Network Logging: SIEM solutions did not capture network connections (Event ID 3), preventing detection of the C2 callback.
4.2 Recommendations:
Email Security Enhancements:
Implement SPF, DKIM, and DMARC to reduce email spoofing and phishing success rates.
Block ZIP attachments containing .lnk files at the email gateway.
Endpoint Detection Improvements:
Enable Sysmon Event ID 1 (Process Creation) and Event ID 3 (Network Connections) with filtering for LOLBins (rundll32.exe, mshta.exe, powershell.exe).
Deploy EDR solutions capable of detecting AMSI bypass attempts and reflective PowerShell loads.
Persistence Detection & Removal:
Implement scheduled scans for HKCU:\Software\Microsoft\Windows\CurrentVersion\Run keys containing suspicious paths or LOLBins usage.
Set up SIEM alerts for registry modifications to common persistence locations.
Network Monitoring:
Deploy SSL/TLS inspection where feasible to detect encrypted C2 traffic.
Create SIEM rules to flag unusual outbound HTTPS connections to uncommon domains or direct IP addresses.
User Awareness & Training:
Conduct phishing awareness training, emphasizing the risks of ZIP file attachments and .lnk files.
Encourage users to report suspicious emails and unusual system behavior.
4.3 Anti-Detection Techniques
Email Delivery Evasion: Sent multiple phishing email variants with ZIP-embedded LNK files to bypass email security solutions.
Payload Evasion: Utilized hash manipulation and non-standard file names to evade signature-based detection.
Execution Technique: Avoided direct PowerShell invocation in later stages; leveraged LOLBins (rundll32.exe, mshta.exe) to blend in with legitimate processes.
Persistence Evasion: Established registry-based persistence using non-suspicious names (AdobeFakeUpdate) to avoid immediate detection.
Network Evasion: Used HTTPS for C2 traffic to bypass simple network-based detections. SSL/TLS encrypted channels hindered traffic inspection.
4.4 Future Considerations:
Test detection efficacy against HTML smuggling and QR code phishing campaigns.
Enable DNS query logging for enhanced C2 detection.
Explore LOLBins abuse detection via application whitelisting and stricter endpoint policies.
Implement PowerShell Constrained Language Mode to limit script execution capabilities.
Review user permissions to limit the ability to modify registry run keys without administrative approval.
5. Appendices
5.1 MITRE ATT&CK Technique Mapping & Visualization
This section provides a visual representation of the attack techniques used in the phishing simulation, mapped to the MITRE ATT&CK framework to highlight which tactics were successfully executed and which were not used in this phase.
5.1.1 Heat Map Table
The heat map helps analyze which MITRE ATT&CK techniques were leveraged in the attack, allowing defenders to identify coverage gaps and prioritize detection improvements for future assessments.
Legend: 🔴 = Used in Attack | 🟡 = Potential Variant | ⚪ = Not Used in This Simulation
Tactic | Technique | MITRE ID | Status |
Initial Access | Spear Phishing Attachment (LNK in ZIP) | T1566.001 | 🔴 Used |
Execution | User Execution (Malicious Shortcut File) | T1204 | 🔴 Used |
Execution | LOLBins Execution via mshta.exe, rundll32.exe | T1218 | 🔴 Used |
Persistence | Scheduled Task | T1053 | ⚪ Not Used |
Persistence | Registry Key | T1547 | 🔴 Used |
Privilege Escalation | DLL Hijacking | T1574.002 | ⚪ Not Used |
Defense Evasion | AMSI Bypass (PowerShell Reflection) | T1562.001 | 🔴 Used |
Credential Access | OS Credential Dumping (LSASS Memory) | T1003.001 | ⚪ Not Used |
Discovery | System Information Discovery | T1082 | ⚪ Not Used |
Lateral Movement | PsExec Remote Execution | T1569.002 | ⚪ Not Used |
Command & Control | Ingress Tool Transfer (Downloading EXE/DLL Payload) | T1105 | 🔴 Used |
Command & Control | Application Layer Protocol (HTTPS/TCP) | T1071.001 | 🔴 Used |
Impact | User Execution: GUI Manipulation (RickRoll Test) | T1491.001 | 🔴 Used |
Key Insights:
8 techniques were successfully used (🔴)** in the phishing campaign.
5 techniques were NOT observed (⚪)** but could be used in future Red Team assessments.
5.1.2 Visual Representation - ATT&CK Navigator JSON
For security teams using MITRE ATT&CK Navigator, the following JSON can be imported to visualize attack coverage.
JSON:
{
"name": "FIN7 Endpoint Threat Detection Emulation - DLL",
"version": "4.6",
"domain": "enterprise-attack",
"description": "Updated ATT&CK Navigator Layer mapping for the phishing-to-C2 attack chain with recommended improvements.",
"techniques": [
{
"techniqueID": "T1566.001",
"tactic": "initial-access",
"color": "#ff6666",
"comment": "Phishing email sent with ZIP/LNK attachment via GoPhish."
},
{
"techniqueID": "T1583.001",
"tactic": "resource-development",
"color": "#ff9966",
"comment": "Weaponization phase: Creation of malicious LNK and PowerShell payloads."
},
{
"techniqueID": "T1204.002",
"tactic": "execution",
"color": "#ffcc00",
"comment": "User opens malicious LNK file, triggering execution."
},
{
"techniqueID": "T1059.001",
"tactic": "execution",
"color": "#ffcc00",
"comment": "LNK executes PowerShell script (payload.ps1) to fetch and run additional payloads."
},
{
"techniqueID": "T1218.005",
"tactic": "defense-evasion",
"color": "#ff9900",
"comment": "PowerShell invokes mshta.exe to execute a malicious HTA file."
},
{
"techniqueID": "T1218.011",
"tactic": "persistence",
"color": "#ff66ff",
"comment": "Rundll32.exe used to execute a DLL payload for persistence."
},
{
"techniqueID": "T1547.001",
"tactic": "persistence",
"color": "#ff66ff",
"comment": "Registry Run Key created to ensure execution of the DLL-based reverse shell."
},
{
"techniqueID": "T1105",
"tactic": "command-and-control",
"color": "#6666ff",
"comment": "PowerShell downloads and registers the malicious DLL (kevin_beacon.dll)."
},
{
"techniqueID": "T1071.001",
"tactic": "command-and-control",
"color": "#6666ff",
"comment": "Meterpreter session establishes C2 over HTTPS."
},
{
"techniqueID": "T1499",
"tactic": "impact",
"color": "#ff0000",
"comment": "RickRoll execution: Forced browser navigation demonstrating endpoint manipulation."
}
],
"gradient": {
"colors": ["#00ff00", "#ff0000"],
"minValue": 0,
"maxValue": 1
},
"legendItems": [
{ "color": "#ff6666", "label": "Initial Access" },
{ "color": "#ff9966", "label": "Weaponization" },
{ "color": "#ffcc00", "label": "Execution" },
{ "color": "#ff9900", "label": "Defense Evasion" },
{ "color": "#ff66ff", "label": "Persistence" },
{ "color": "#6666ff", "label": "Command & Control" },
{ "color": "#ff0000", "label": "Impact" }
]
}5.2 Attack Execution Flow
This section provides a visual representation of the phishing attack lifecycle, showing how the payload progressed from initial delivery to execution and simulated command & control (C2) activity.
5.2.1 Attack Flow Diagram
The diagram below outlines the sequential flow of the attack, mapping each stage to its corresponding MITRE ATT&CK technique.

5.2.2 Attack Flow Breakdown
The following breakdown details each step of the attack, describing the techniques used, execution process, and potential detection opportunities.
🔴 Step 1: Phishing Email Sent
Technique: T1566.001 – Spear Phishing Attachment (Initial Access)
Description:
The attacker sent a phishing email using Gophish via Postfix.
The email contained a ZIP attachment (bait.zip) with a weaponized LNK file (Fake_Invoice_2024.pdf.lnk).
The LNK file masqueraded as a legitimate document but was crafted to execute malicious PowerShell commands upon opening.
🔴 Step 2: Email Delivered to Target Inbox
Description:
The phishing email successfully reached the target’s inbox (blue-edr-bob) without being flagged by email security solutions.
The victim observed an attachment named bait.zip, which contained the malicious LNK file.
🔴 Step 3: User Opens Email & Runs LNK Payload
Technique: T1204.002 – User Execution: Malicious File (Execution)
Description:
The user unzipped and double-clicked the LNK file (Fake_Invoice_2024.pdf.lnk).
This action triggered PowerShell to execute hidden commands, fetching and running the first-stage payload (payload.ps1) from a remote server.
🔴 Step 4: LNK Executes PowerShell Script (payload.ps1)
Technique: T1059.001 – Command and Scripting Interpreter: PowerShell (Execution)
Description:
The PowerShell script (payload.ps1) leveraged IEX (Invoke-Expression) to load code into memory, evading disk-based detection.
It fetched a malicious HTA file (malware.hta) to execute the next stage.
🔴 Step 5: PowerShell Switches to MSHTA.exe
Technique: T1218.005 – System Binary Proxy Execution: MSHTA (Defense Evasion & Execution)
Description:
The HTA file was executed via mshta.exe, a trusted Windows utility often abused for defense evasion.
This pivot from PowerShell to MSHTA enabled bypassing certain security solutions.
🔴 Step 6: MSHTA.exe Switches Back to PowerShell.exe
Technique: T1218.011 – System Binary Proxy Execution: Rundll32 (Defense Evasion & Execution)
Description:
The HTA payload invoked powershell.exe again to fetch stage2dll.ps1.
This script was loaded directly into memory, continuing the in-memory execution chain to avoid detection.
🔴 Step 7: AMSI Bypass, Beacon Download & Registry Key Persistence
Techniques:
T1562.001 – Defense Evasion: Disable or Modify Tools (AMSI Bypass)
T1105 – Ingress Tool Transfer (Delivery of the Beacon)
T1547.001 – Persistence: Registry Run Keys/Startup Folder (Persistence)
Description:
The stage2dll.ps1 script:
Disabled AMSI (Antimalware Scan Interface) to prevent script scanning by Windows Defender.
Downloaded the C2 beacon (kevin_beacon.dll) to the Public directory.
Created a persistence mechanism by registering the DLL under the AdobeFakeUpdate Run registry key.
🔴 Step 8: C2 Beacon Execution & Connection Established
Technique: T1071.001 – Application Layer Protocol: Web Protocols (HTTPS) (Command & Control)
Description:
Upon registry key execution, rundll32.exe launched kevin_beacon.dll.
The beacon successfully connected back to the C2 server (red-c2-kali) over HTTPS.
The attacker established a Meterpreter session, gaining full remote control of the victim’s system.
🔴 Step 9: RickRoll Execution (Impact Demonstration)
Technique: T1491.001 – Defacement: Internal Defacement (Impact)
Description:
To demonstrate post-exploitation control, the attacker forced the victim’s browser to open:
This RickRoll payload served as a safe, non-destructive demonstration of successful compromise.
TL;DR
Red Team phishing simulation bypassed email security, achieved 100% payload delivery and execution, successfully established C2 connections via HTTPS, and demonstrated registry-based persistence. SOC detection delays and lack of outbound C2 monitoring revealed key SIEM and endpoint detection gaps.
Download PDF:
Other Reports in This Project
✔ Red Team: Simulated a FIN7-inspired endpoint attack using LNK payloads, PowerShell execution, and C2 channels to test detection gaps.
✔ Blue Team: Developed Sysmon, Splunk, and LimaCharlie EDR detection rules, reducing detection time to under 1 minute and containment to 5 minutes.
✔ Purple Team: Quantified risk reduction of $58K per incident, aligned defenses with NIST 800-53, ISO 27001, and improved SOC response efficiency.
✔ Setup Guide: Configured attack and defense environments with Gophish, Metasploit, Sysmon, and Splunk for consistent, repeatable testing.


